To How Xss
How To Check For Gowebsite Online Scripting Xss
Cross-site scripting (xss) stays one of the most common security vulnerabilities presently located in net-applications. this article gives perception into how to check your packages for cross-website online scripting (xss) defects using both manual and automated method. Move website online scripting prevention cheat sheet introduction. this newsletter provides a simple tremendous version for stopping xss using output escaping/encoding properly. while there are a huge range of xss assault vectors, following some simple guidelines can absolutely defend in opposition to this serious attack. Relying at the functionality and data processed via the vulnerable utility, xss vulnerabilities can pose a massive danger to the commercial enterprise. attackers could scouse borrow exclusive information, carry out unauthorized activities, and take over the entire internet periods of the sufferer users. improvement on this put up, we are able to study a way to allow server-facet caching in expressjs examine on
redos vulnerabilities in npm spikes via 143% and xss maintains to develop
snykio/
In this xss academic i'm able to provide an explanation for the fundamentals of move site scripting and the harm that could achieved from to how xss an xss assault. many human beings treat an xss vulnerability as a low to medium danger vulnerability, when in reality it's far a dangerous attack that may lead to your customers being compromised. Xss locator (polygot) the following is a “polygot test xss payload. ” this check will execute in multiple contexts which includes html, script string, js and url.
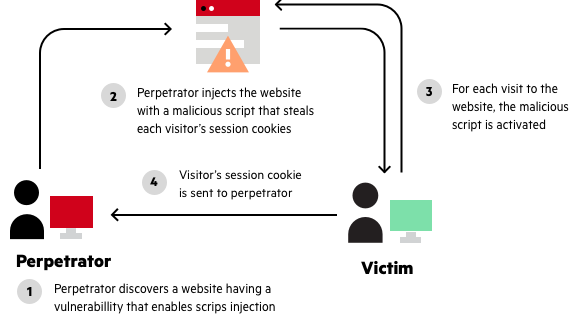
Move-website online scripting (xss) is a sort of pc safety vulnerability typically located in web packages. xss assaults enable attackers to inject customer-facet scripts into net pages regarded by different customers. a pass-web site scripting vulnerability can be utilized by attackers to skip get right of entry to controls which includes the identical-starting place coverage. move-web site scripting carried out on websites accounted for roughly 84%. Cross-site scripting (xss) attacks are a kind of injection, wherein malicious scripts are injected into in any other case benign and depended on websites. xss assaults arise when an attacker makes use of a web application to send malicious code, commonly within the form of a browser facet script, to a different end consumer. Xss what is pass-site scripting? pass-web page scripting (also referred to as xss) is one of the maximum not unusual software-layer web attacks. xss vulnerabilities target scripts embedded in to how xss a page which might be finished at the consumer-facet (inside the person’s internet browser) as opposed to at the server-aspect. embedding in xml; it’s hard to see how that api ought to do in any other case the launchpad integration code accordingly makes use of tal code alongside these lines, the use of the structure keyword to explicitly indicate that the excerpts in question do not require html-escaping (like most properly net frameworks, tal’s default is to break out all variable content material, so a hit xss attacks on launchpad have traditionally been rare): A meditated xss (or also referred to as a non-chronic xss attack) is a selected type of xss whose malicious script bounces off of some other website to the victim’s browser. it's miles exceeded within the query, normally, within the url. it makes exploitation as easy as tricking a user to click on on a hyperlink. compliance how a huge rock revealed a tesla xss vulnerability jeremy kirk • july sixteen, 2019 compliance unexpected password tips from nist mike wilson • july 15, 2019 ► compliance the way to defend ssh keys ► compliance constructing a framework for Stored cross-website online scripting. saved xss (additionally known as continual or 2nd-order xss) arises while an application receives data from an untrusted source and consists of that facts within its later http responses in an unsafe way.. the information in question might be submitted to the application through http requests; as an example, feedback on a blog publish, consumer nicknames in a chat room, or touch information on. Cross web site scripting (xss) is a common assault vector that injects malicious code into to how xss a inclined net utility. xss differs from other net assault vectors (e. g. sq. injections), in that it does not at once target the utility itself. as an alternative, the users of the net software are those at. Cross-website online scripting assaults (xss) can be used by attackers to undermine application protection in lots of methods. it's far most usually used to steal consultation cookies, which permits the attacker to impersonate to how xss the sufferer. similarly to that, xss vulnerabilities were used to create social networks worms, spread malware, deface websites, and phish for credentials. Depending at the functionality and facts processed by means of the prone application, xss vulnerabilities can pose a great risk to the commercial enterprise. attackers ought to steal confidential information, carry out unauthorized sports, and take over the whole internet sessions of the victim users. Go-site scripting (additionally called xss) is one of the maximum commonplace software-layer internet assaults. xss vulnerabilities goal scripts embedded in a web page that are completed at the patron-aspect (inside the consumer’s net browser) in place of at the server-facet. insecure wep application please (oriwap) nancy snoke knowledge xss christina mitchell social engineering at work a way to use fine influence to gain management buy-in the firewall can’t protect you from malware, to how xss xss and square-injection assaults modsecurity will help to improve the security of your server and scripts you're the use of on it a way to speedy find from ssh which rule identity A entire manual to cross web site scripting (xss) attack, the way to prevent it, and xss checking out. go web page scripting (xss) is one of the maximum popular and inclined assaults which is thought by using each advanced tester. it's miles taken into consideration as one of the riskiest attacks for the net applications and can deliver dangerous effects too. can also eight, 2018 what's move-website online scripting (xss) assault and a way to prevent it muhammad haad ahmed june three, 2013 Because it seems, there are at the least two common ways of causing a victim to release a reflected xss attack in opposition to himself: if the user goals a specific individual, the attacker can send the malicious url to the victim (using email or if the person objectives a massive group of humans, the attacker can. Xss vulnerabilities are commonplace enough to have graced packages as large and popular as facebook, google, and paypal, and xss has been a mainstay at the owasp top 10 list considering that its inception. xss vulnerabilities are in particular risky because an attacker exploiting an xss assault can benefit the capacity to do regardless of the person can do, and to peer. Stored go-web page scripting. saved xss (additionally referred to as continual or 2nd-order xss) arises while an utility gets information from an untrusted source and includes that information within its later http responses in an unsafe way.. the facts in question might be submitted to the utility through http requests; for instance, feedback on a blog publish, consumer nicknames in a talk room, or contact details on. See more videos for how to xss. Move-website online scripting (xss) assaults are a type of injection, wherein malicious scripts are injected into otherwise benign and depended on web sites. xss assaults occur when an attacker uses an internet software to send malicious code, normally inside the form of a browser aspect script, to a different give up user. Pass-web page scripting (xss) is a customer-facet code injection attack. the attacker ambitions to execute malicious scripts in an internet browser of the victim via including malicious code in a legitimate net web page or web application. the actual attack occurs whilst the sufferer visits the net web page or internet application that executes the malicious code. Extra xss by jakob kallin and irene lobo valbuena is licensed underneath a creative commons attribution-sharealike three. 0 unported license. the supply code for excess xss is to be had on github. excess xss become created in 2013 as part of the language-based security route at chalmers university of technology. To recognize the way to save you move-site scripting (xss), see the item entitled: “how to save you cross-website scripting (xss)“. sources of untrusted input it's miles crucial which you do not forget about potential resources of untrusted input, as doing so may also mean you neglect a potential hassle. The actual xss attack is shaped by injecting unsanitised input into a web utility. the input is generally inside the form of javascript, that can be stored via the utility and back to other users once they visit the web page. thereby executing the javascript within the customers browser.Contemplated Xss Explained How To Save You Reflected Xss In
Infosec Careers Information Training Education Careersinfosecurity

Komentar
Posting Komentar